Introduction
DevOps brings several value-added benefits. From enhanced agility, faster time to market, and reduced costs to dynamic provisioning. serverless computing, and flexible pay-as-you-go plans. But all these gains can go for a toss in an instant if “Security” is not your top priority.
So, if you leverage DevOps for better productivity and enhanced client satisfaction while ignoring security issues, you will end up carrying water uphill in a sieve! To headstart, this blog offers a complete rundown of everything you need to know to implement a smart DevSecOps strategy.
So let’s start the blog by knowing about DevSecOps.
What is DevSecOps?
Modern enterprises are leveraging the collaborative approach of DevOps to automate rapid and reliable product delivery. But what about security? How are they mitigating vulnerabilities in the software development lifecycle? DevSecOps is their strategy!
The goal is to implement checks on the same scale as app development. This approach eliminates the possibility of a threat at a later stage which would otherwise call for reworking countless lines of code – a tedious, time-consuming, and labor-intensive process!
Enterprise adopt this strategy because:-
- Security is built into the product; not treated as an afterthought.
- This ensures transparent workflows and timely collaboration during the development.
- It facilitates faster recovery in case a threat is detected.
Why DevSecOps Should be Your Top Priority?
Any glitch in security measures can invite a major loss of revenue and reputation. The risks of being relaxed patches are immediate and very expensive.
By implementing DevSecOps proactively businesses can achieve unrivaled success.
Faster time to market – 12 times faster in fixing flaws as compared to traditional practices.
Increased Revenue – with the implementation of DevSecOps business organizations increase their profit by 50%.
Competitive Advantage – 4.8 times improvement in performance rates,
The business case for DevSecOps is crystal clear. It drives performance, profit, and prominence!
Benefits of DevSecOps
- Automates securing of code to reduce vulnerabilities in apps while enabling predictable processes.
- Issues can be identified & resolved much faster in the early stages of the SDLC (Software Development Life Cycle)
- Helps ensure and maintain compliance in the CICD pipeline from day one
- Offers more agility and pace to the assigned teams
- Enhances trust and transparency between teams right from the start
- Increases the delivery rate and reduces costs
- Facilitates consistent security with automation tools for testing and reporting
- Creates an immutable environment that takes up lesser hands-on time for account management, event monitoring, assessing vulnerability, code security & deploying checks
- Enables security professionals to focus their efforts and attention on remediating threats and eliminating the risk
Key Components of DevSecOps Strategy:-
Enterprises need to adopt a cultural and technical mindset when leveraging this strategy to address their real-time threats. A practical one has 6 key components.
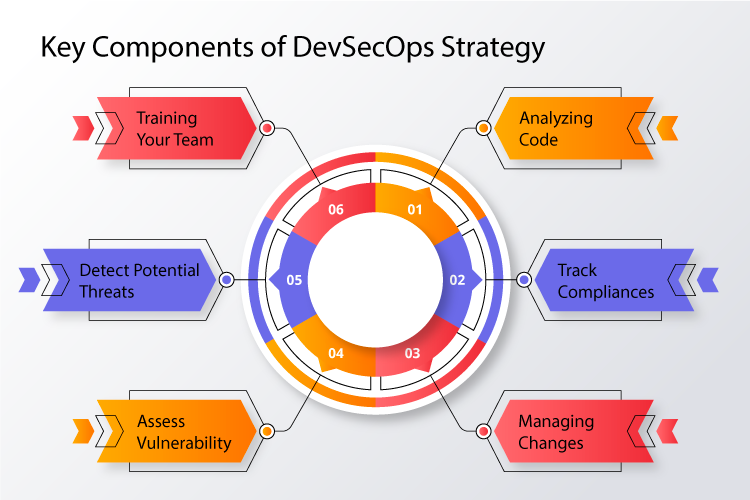
Analyzing Code:-
Identify vulnerabilities on time with the delivery of code in small, manageable chunks.
Track Compliances:-
Ensure compliance with all applicable regulations including Payment Card Industry Digital Security Standard (PCI DSS) and General Data Protection Regulations (GDPR) and always be prepared for regulatory audits.
Managing Changes:-
Submit changes that can accelerate the development speed and efficiency. Also, determine if the outcome of changes is favorable or not.
Assess Vulnerability:-
Systematically review all weaknesses that can leave the system vulnerable. Define and delegate security levels to known weak points and recommend corrective action as and when needed.
Detect Potential Threats:-
Every code update accompanies impending threats. Moreover, It is vital to uncover these threats at the earliest and respond promptly.
Training Your Team:-
Involve your development and IT-ops teams in security-related training and equip them with the standard operating guidelines for set workflows.
Pitfalls of DevSecOps and Best Practices to Overcome
A DevOps model typically involves cross-team collaboration. This brings in different workflows, specifications, and approaches around planning, coding, deploying, testing, integration, infrastructure management, and more.
Additionally, there is continuous integration monitoring and automation across the complete process chain. All of this results in fast-paced development cycles, accelerated release time, and concise feedback loops. This dynamic environment can create gaps between the DevOps and the Security teams.
DevSecOps Challenges
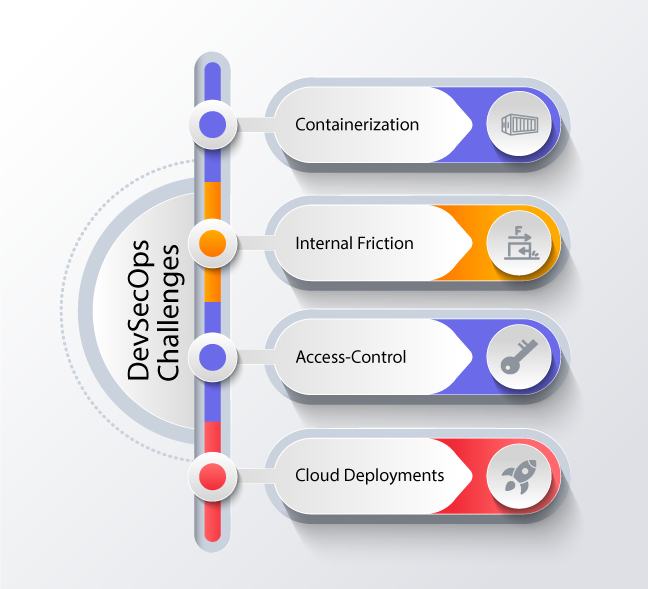
Containerization
Container tools boost productivity but the same tools can also invite security issues. While containerizations bring you the agility to run on any cloud platform independently, it gives rise to challenges if you are not using proper controls. Above all, container tools share the operating system, and they are rarely checked for vulnerabilities.
Internal Friction
Cultural resistance often crops up a key issue of concern when addressing challenges in DevOps. This is often supported by the argument that special checks derail the development cycle. But in reality, addressing security concerns early on takes up much less time than taking a reactive approach at the last minute.
Access-Control
DevOps is a hyper-connected, dynamic and collaborative approach. Teams keep sharing credentials, APIs, SSH keys, tokens, and other critical information. Moreover, this data is passed across containers, cloud instances, apps, and open-source platforms.
These platforms are susceptible to attacks and so, the assets passing through them are also subject to threats. This can give intruders control over data and systems, inviting serious issues.
Cloud Deployments
The DevOps team essentially relies on open-source tools and cloud deployments to tackle security and server issues. Such a fast-paced environment often gives rise to erroneous configurations, compliance issues, and compromises mission-critical information leading to breaches.
Best Practices for DevOps Security
Here are some of the best and proven DevOps Security practices.
Implementing Security Policies
Implementing strict enforcement policies is the key to ensuring secure DevOps. Rolling out transparent cybersecurity regulations that are comprehensive and simple to execute for the teams. Moreover, this will simply help them in planning their wor
Verify All Approved Tools
It is equally crucial to consistently verify all the approved tools, accounts, and devices spotted during the discovery phase when you are detecting and mapping the issues. Moreover, be sure to highlight them under security measures that are aligned with your internal guidelines.
Enforcing Configuration Scans
Misconfigurations are a serious issue that can hit an organization’s workflow. Maintaining and monitoring configuration scans across individual builds and serves for all cloud assets consistently. All issues must be addressed in line with the best industry practices.
Automating Security Features
Automating security tools minimizes the risk of errors occurring due to repeated instances inviting downtime issues. Scaling features also help detect vulnerable code and impending threats or other issues within the environment. It also disrupts cultural resistance and reinforces the implementation of DevOps security practices in the process chain.
Monitoring and Managing
Secure all privileged account details and remove administrator rights on the user side to ensure a seamless workflow. Simultaneously, keep an eye on the privileged sessions to ensure legitimacy and adherence to compliance regulations.
Restrict access only to production systems while giving internal teams the authority to design, deploy, and resolve development issues. Moreover, leverage access management resources to track and audit
Ensuring Secure Access
Be sure to delete all the credentials that are embedded in files, code, service accounts & cloud platforms. Store them safely at a centralized location where they can be accessed using privileged password management solutions. Moreover, leveraging such API calls ensures total control over embedded keys, code, and scripts.
Integrating Security Across SDLC
Implementing the DevSecOps model brings you the advantage of cybersecurity measures such as firewalls, identity access management, code review, and vulnerability management. This governance ensures a secure DevOps environment ensuring seamless and speedy delivery.
As per the above-mentioned security measures, it is crystal clear that security creates a solid foundation for a full-fledged DevOps implementation. With issues addressed, it is undeniably a game-changer that efficiently caters to fast-changing business needs.
DevOps Tools Which CodeStore Technology Uses For Providing Better Solutions to Clients

Terraform
This is an open-source infrastructure as a code software tool allowing DevOps engineers to programmatically provision the physical resources an application requires to run.
Infrastructure as code is an IT practice that manages an application’s underlying IT infrastructure through programming. This approach to resource allocation allows developers to logically manage, monitor, and provision resources – as opposed to requiring that an operations team manually configure each required resource.
Docker
The CodeStore team basically uses Docker to create, deploy, and run applications by using containers. Through Docker DevOps, developers can pack all parts of an application like libraries and other dependencies easily and ship it out as a single package.
The package delivery of the application can keep the developer assured about the timely delivery of the application without being concerned about the type and configuration of the platform.
Jenkins
Continuous integration is the most important aspect of DevOps that is used to integrate various DevOps stages. Jenkins is one of the most famous Continuous Integration tools, written in Java with plugins built for Continuous Integration purposes.
Moreover, with Jenkins, organizations can accelerate the software development process through automation. This integrates development life-cycle processes of all kinds, including build, documentation, test packages, stage, deploy, static analysis, and many more.
Kubernetes
Kubernetes is a very reliable container cluster management tool. Above all, cluster computing affords DevOps various benefits over other computing environments. Kubernetes, a self-healing, fast container cluster management tool, guarantees developers and engineers in providing faster performance, better redundancy, and excellent uptime.
Bottom Line
As a trusted and top-rated DevOps service and solution provider, the CodeStore team leverages an industry-leading technology stack to achieve speedy deployment without compromising on software quality and security.
Our full-scale service focuses on providing industry-specific consultations, custom implementation, automation, and management-driven by proven methodologies that deliver best-in-class software.
The most powerful tech stacks backed our team of efficient developers based on their experience. They also have experience with tools like Kubernetes, Jenkins, Docker, and more to enable secure and seamless implementation.
We will help you in embedding DevOps security across every stage of the delivery pipeline while ensuring that all the tools and technologies are aligned with your regulatory requirements.
If you have any requirements and queries then feel free to share the same with us at sales@codestoresolutions.com

